This post is part of a series of AWS related posts.
Intro
The AWS Solution Architect Associate (SAA) is an associate level certification,
which is positioned between the foundational and professional level.
It is a prerequisite to attain the AWS Solution Architect Professional (SAP) certification
and has the exam code SAA-C02.
The suffix C02 is the version of the exam and is an incrementing counter.
At the time of writing this post, AWS does not provide a nice online course like it does for the AWS Cloud Practitioner. However, there are plenty other offers.
I’ve chosen the Udemy Ultimate AWS Certified Solutions Architect Associate 2022 online course to prepare for the exam.
The following notes are complementary to the Udemy course referenced above. To pass the AWS SAA-C02 exam, I found it useful to know the course information as well as the complementary notes. The chapter titles in this post are the same as in the course and you will only find the ones that required me to add my own notes.
Section 3: Getting started with AWS
- AWS infrastructure overview: infrastructure.aws
- AWS Regional services: aws.amazon.com
Section 4: IAM & AWS CLI
- AWS does not allow nested groups; groups only contain users
- AWS (root) Account
- Creating an AWS root account is the same as creating an account that can be added to an AWS organization (via invite). A root user account IS the account used to open an AWS account.
Section 5: EC2 Fundamentals
- In order to give a cloud resource a name, set the
nametag - EC2 instance types
- EC2 instance types overview: https://instances.vantage.sh/
- EC2 instance connect: web app to SSH into EC2 instances
- Spot Fleet: a set of Spot Instances and optionally On-demand Instances
- EC2 Nitro: new virt. tech (allows 64k IOPS, while non-nitro only allows 32k IOPS)
Section 7: EC2 Instance Store
- Instance Store
- Faster than EBS, because directly attached as local harddrive to server
- Only for temporary data, because it is not backed up (docs)
- Use case: local cache with high IOPS
Section 8: High Availability & Scalability: ELB & ASG
- ALB traffic to backend has source IP address of ALB
- NLB traffic to backend has source IP address of request origin (e.g. client in internet)
- it forwards packets on layer 4
- requires different security group configuration
- AWS Auto Scaling Group
- Launch template: configure everything, including what instance types to launch
- Launch configuration: OBSOLETE. Subset of launch template features
- High-Availability
- does not mean “instant access” to data
- A HA storage requirement does not mean the data needs to be instantly accessible; ie AWS Glacier is a HA storage
Section 12: Amazon S3 Introduction
- Versioning
- versions are not incremental values (e.g. v1, v2), but random identifiers (e.g.
SD8342DKJWBD) - if versioning is enabled with existing files, the version of the files will be
NULL, only newly uploaded files get version tags
- versions are not incremental values (e.g. v1, v2), but random identifiers (e.g.
Section 13: AWS SDK, IAM & Policies
- Policy simulator: https://policysim.aws.amazon.com/
- test your policy
- Access EC2 instance metadata from within instance: http://169.254.169.254/latest/meta-data/
- access key id & secret of roles assigned to the instance are accessible this way
Section 14: Advanced Amazon S3
- default encryption
- it encrypts files that are uploaded unencrypted, but you can also upload encrypted files using different encryption settings than default
Section 26: Identity & Access Management (IAM) - Advanced
Identity-based policy: permissions (policy) are assigned to users, groups or rolesResource-based policy: permissions are assigned to service & the requesting principal does not have to give up its permissions
Roles are assumed temporarily by services and users.
Resource-based policies are helpful in cross-AWS account scenarios, for example, when a user from Account A has to fetch data from an S3 bucket and push that data to an S3 bucket in Account B. Where in Identity based policies you state what they can access, Resource based policies say what can access them.
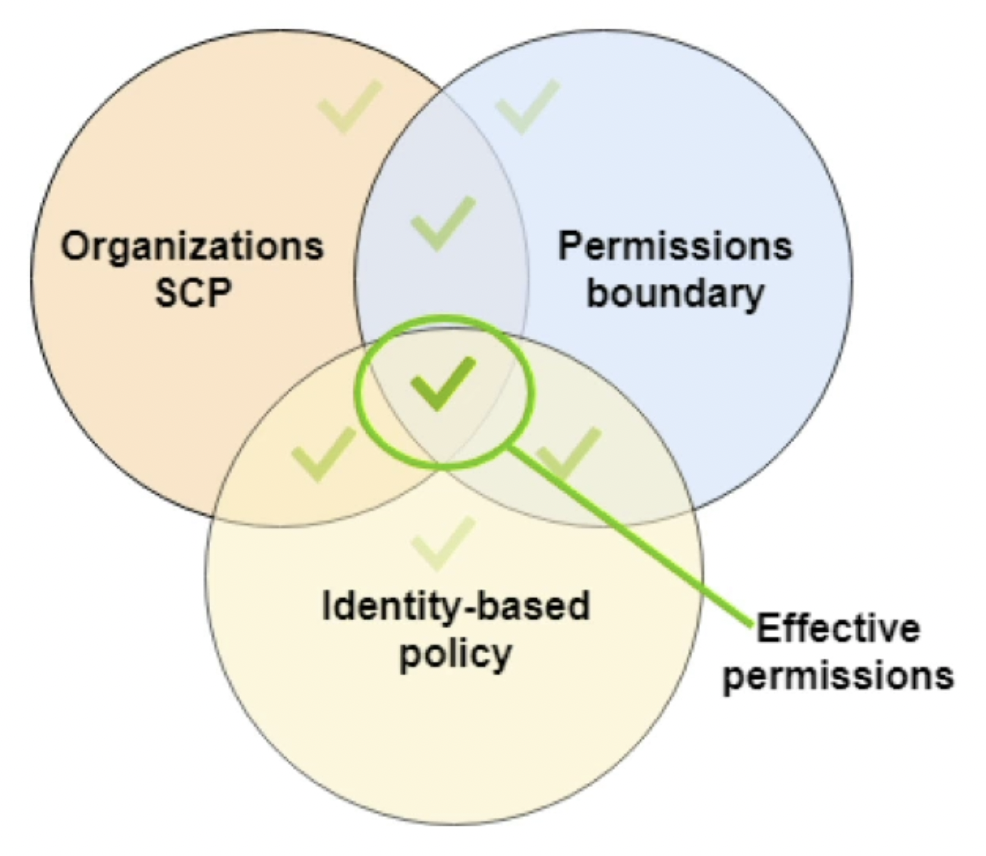
Permission Boundaries
Permission boundaries are like Mandatory Access Control - they override the (DAC) permissions. In this context, DAC permissions are just normal IAM policies that get attached to a user. For example, if an IAM policy grants a user S3 listObject and the boundary policy does only allow access to EC2, then the user has no S3 permissions.
A useful scenario is to set permission boundaries so that a developer can assign himself permissions, but NOT administrative access.
Policy Evaluation Flow
IAM policy evaluation flow (helpful for debugging).
Explicit deny in a policy overrides explicit allow!
AWS SSO
AWS SSO is a service that can manage access for users to AWS accounts and external apps, such as DropBox, etc. Users can be stored in AWS SSO itself or, MS AD, etc. Users cannot be stored in Cognito User Pools, because AWS SSO is to access AWS infra, while Cognito is a service for your customers to access your apps.
Section 27: Security
- RDS auth: username & password OR enable IAM DB Auth to enable short lived tokens
KMS
By default, when an AWS KMS key is generated, it has no permissions. No IAM admin or user can use it. So, we have to create a KEY POLICY (a resource-based policy). This policy allows to create IAM policies that manage access to the key. KEY POLICIES are distinct from IAM policies.
An example KEY POLICY that allows IAM POLICIES:
{
"Sid": "Enable IAM policies",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111122223333:root"
},
"Action": "kms:*",
"Resource": "*"
}
The :root alias means that any IAM user of account 111122223333 is affected by this policy. Hence every IAM user, with respective IAM policies, has access to the key.
So, two policies are needed to access a KMS key. The key policy that allows IAM policies to grant access to the key and the IAM policies that grant a user access to the key.
Resource-based policies have the characteristic that they grant access to a principcal.
Section 28: Networking
- AWS max. CIDR size is:
/16(no customer gets/8or bigger) - 5 hosts per network range are reserved for AWS, remember that when calculating network sizes
- VPC Endpoints are free of charge and are always cheaper than using a NAT gateway & Internet Gateway to connect to AWS global services
Exam
For exam preparation, I solved all the example questions by AWS and purchased a practice question set. After completing two practice exams, I felt prepared well enough and took the exam 👨🎓.
I didn’t deploy a particularly sophisticated exam strategy to be honest. If I felt that a question (and their multiple choice answers) takes too much time to read, I’d just skip it and do it at the end, which helped me greatly with time management. Like for the CLF exam, I watched out for distractors and, whenever I wasn’t sure about my answers, I’d mark the question for later review.
A hint for the exam: global is an important keyword (as in “global application”), it means that regional constructs, such as load balancers, are insufficient and the answer looks for global services, such as CloudFront or Global Accelerator.
Practicing
Before and after the exam, I applied my knowledge by deploying some simple solution architectures using Cloudformation. This helped me to memorize what I just learned and also served as a preparation for the SAP exam.
EC2 & EFS Deployment
The first architecture depicts two EC2 instances in different availability zones that have the same EFS file system mounted:
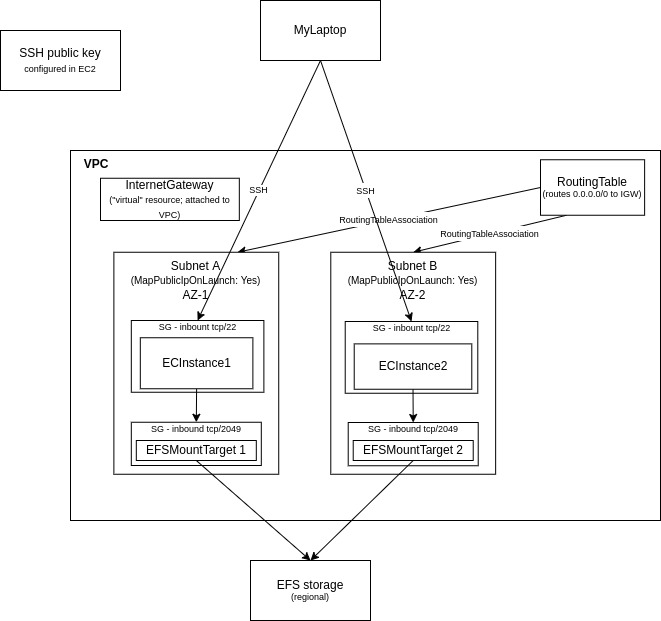
You can find the CloudFormation template here.
Lambda Deployment
The second architecture diagram documents the usage of Lambda functions behind an Application Load balancer:
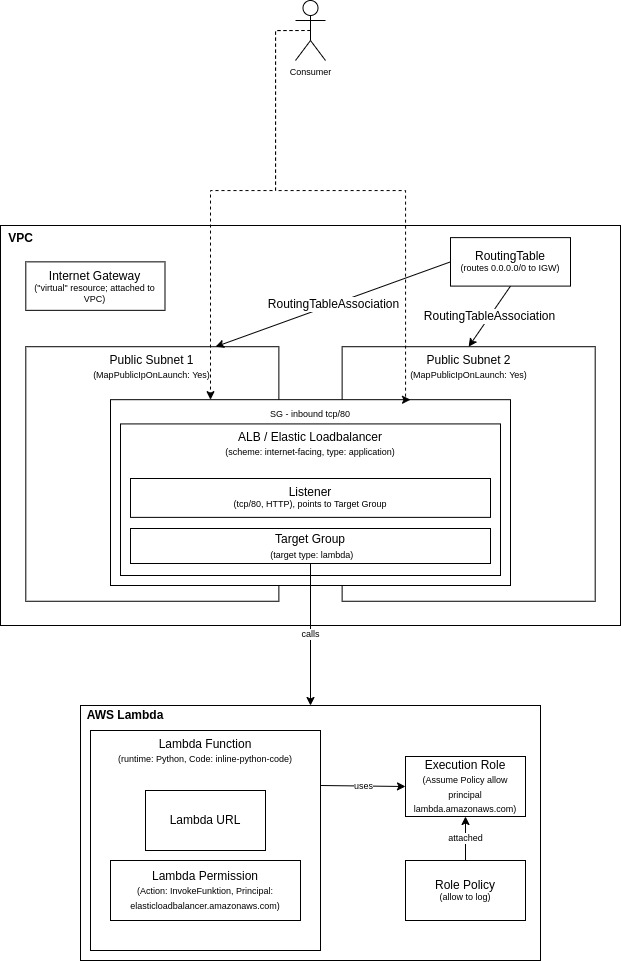
You can find the CloudFormation template here.